04. Introduction to Encryption
Introduction to Encryption Heading
Introduction to Encryption
ND545 C02 L04 A04 Introduction To Encryption Part 1 V2
Introduction to Encryption Notes
Recap:
- Encryption has been around, in various forms, for thousands of years.
- Sometimes encryption only needs to work for a short time, the data isn't relevant after the transaction has processed.
Key Terms
- Encryption: is the process that converts plaintext, or text that can be read by anyone, into ciphertext and it can only be read by the person who has the secret code, or decryption key.
- Plaintext: data that represent only characters of readable material.
- Ciphertext: is encrypted text modified from plaintext using an encryption algorithm.
- Algorithm: a process or set of rules to be followed in calculations or other problem-solving operations, especially by a computer.
Introduction to Encryption Image
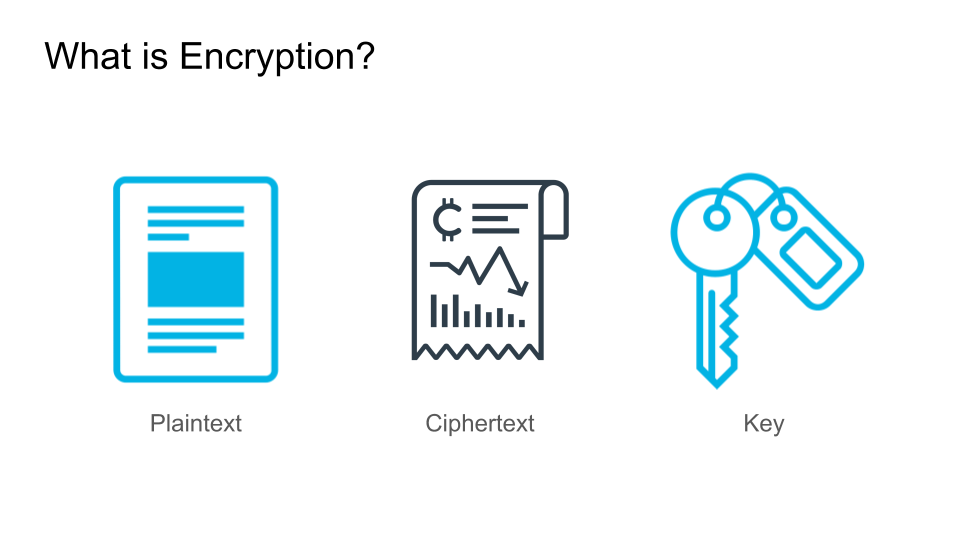
What Is Encryption?
Symmetric Encryption
ND545 C02 L04 A04 Introduction To Encryption Part 2
Recap:
- Two types of Symmetric encryption algorithms:
- Block Algorithms.
- Stream Algorithms.
- Types of Symmetric Encryption:
- AES Advanced Encryption Standard.
- Twofish
- RC4 Rivest Cipher 4.
- Symmetric Strengths and Weaknesses:
- Very Fast.
- Each party already has the key so the data can be transmitted in any manner.
- Key transport is difficult. The only true secure way is to hand it from person to person.
- Once key is exchanged there is no identity verification as to who has the key.
Key Terms
- Symmetric: is a type of encryption where only one key (a secret key) is used to both encrypt and decrypt electronic information.
- Block Algorithm: is a deterministic algorithm operating on fixed-length groups of bits, called blocks.
- Stream Algorithm: each plaintext digit is encrypted one at a time.
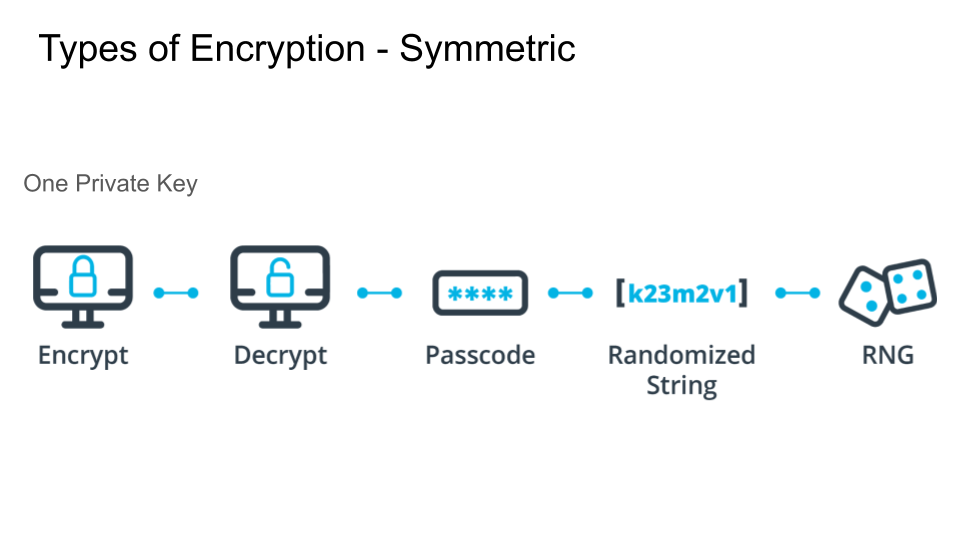
Symmetric Encryption
Asymmetric Encryption
ND545 C02 L04 A04 Introduction To Encryption Part 3
Recap:
- With Asymmetric Encryption, keys are in pairs.
- Public Key Infrastructure is the key management system.
- PKI uses Digital Certificates to verify identity.
- Some Types of Asymmetric Encryption:
- RSA Rivest Shamir Adleman
- Diffie-Hellman
- Asymmetric Strengths and Weaknesses :
- Authentication, allows you to verify the identity of the sender/recipient.
- Private Key never needs to be shared.
- Slower than Symmetric.
- By requiring a Certificate Authority it creates the need to trust a 3rd party.
Key Terms
- Asymmetric Encryption: is a cryptographic system that uses pairs of keys: public keys, which may be disseminated widely, and private keys, which are known only to the owner.
- Public Key Infrastructure: is a technology for authenticating users and devices. The basic idea is to have one or more trusted parties digitally sign documents certifying that a particular cryptographic key belongs to a particular user or device.
- Authentication: the process or action of verifying the identity of a user or process.
- Certificate Authority: is an organization that acts to validate identities and bind them to cryptographic key pairs with digital certificates.
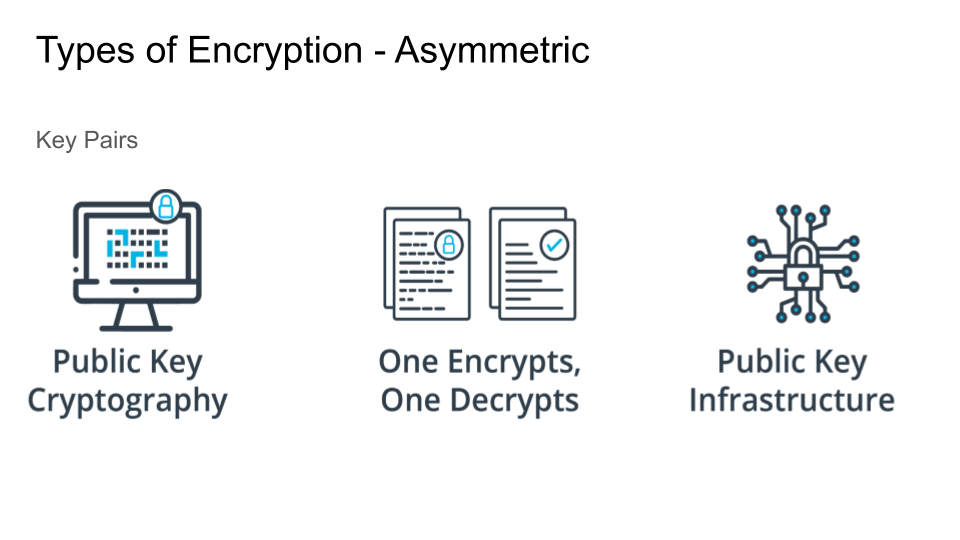
Asymmetric Encryption
Use Cases
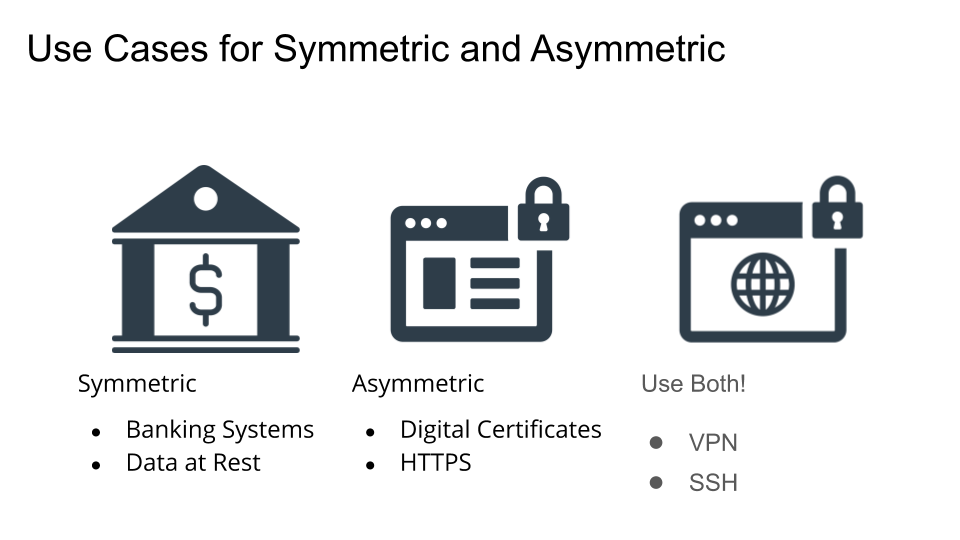
Use Cases for Symmetric and Asymmetric Encryption
ND545 C02 L04 A05 Introduction To Encryption Walkthrough
Try it Out
Below is the code from the video above. Give it a try. You can also copy and paste into your own Python editor if you like!
Code
If you need a code on the https://github.com/udacity.
Introduction to Encryption Further Research